z/OS with vault-style credential mapping
In this model, users are authenticated in a vault-style environment. Figure 1 illustrates this environment:
Figure 1. Web Express
Logon in a vault-style environment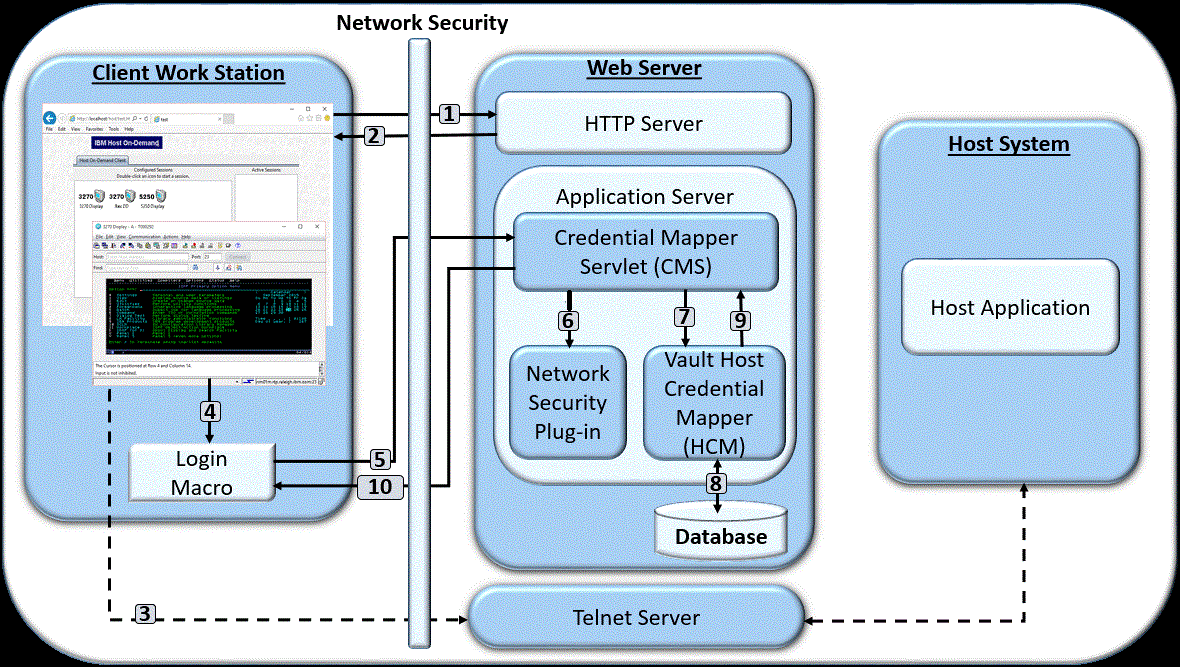

- The user clicks a link to launch the Z and I Emulator for Web desktop, which sends an HTTPS request through the network security application to the Web server.
- The Web server returns the HTTPS request and the Z and I Emulator for Web desktop displays.
- The user launches a host session.
- The login macro executes.
- The macro sends an HTTPS request to the CMS to obtain the host credentials.
- The CMS retrieves the user's network ID from the Network Security plug-in.
- The CMS passes the network ID and application ID to the Vault HCM plug-in.
- Using the network ID and application ID, the Vault HCM plug-in calls upon a database, such as IBM DB2, to map the user's host ID and password.
- The Vault HCM plug-in passes the user's host ID and password to the CMS.
- The CMS returns the host credentials to the client as an XML document.